Table of contents
Backup What Page Overview
- Backup What page allows users to specify the combination of a Host and Directories on it that need to be backed up periodically.
- ZMC refers to the combination of Host and Directory combination as a Disk List Entry (DLE).
- An Enterprise typically has a number of servers running different operating systems.
- ZMC is quite capable of running on a single server and backing up the whole or portion of the Enterprise Computing machines.
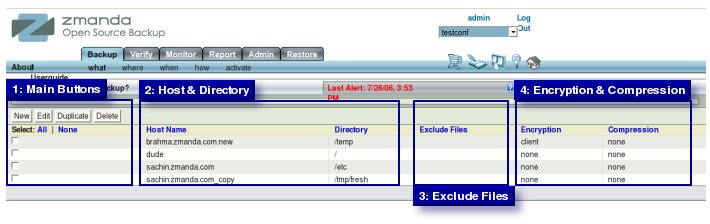
- Box 1 Main Buttons.
- The four main buttons of the page, "New Edit Duplicate Delete" are shown in the left hand side enclosed in Box 1.
- Box 1A Check Boxes.
- New button works without ticking any check box.
- Tick check boxes in Box 1A for Edit, Duplicate and Delete buttons to work.
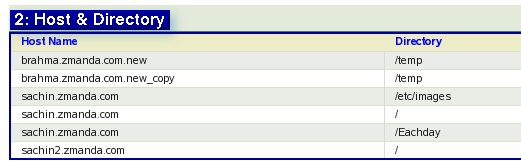
- Box 2A. Host Name.
- When a user is making the first Backup Set, there will be no data displayed.
- When a user is working with an existing Backup Set, its existing data will be displayed.
- Host Name (i.e. Client Host that the user is Backing up) will be displayed in Box.2A.
Warning: Host Names and Directory names are case sensitive. For the Backup to happen, the Host name must correspond to a DNS entry that the Backup Set will look up on the ZMC server. The Directory name must correspond to a directory on the particular host. The Directory path must be absolute one and not a relative path. Otherwise, it will not be backed up.
TIP: Use fully qualified host name while entering the name of the local host as a client. If not ZMC will give a warning at the time of running the Verify Client check.
- Box 2B. Directory.
- The Directory on the Host previously specified that is to be backed up is entered in Box. 2B.
- All directories/files below the directory specified are automatically included in the backup.
TIP: When Tape is the Backup Media, carefully consider using multiple top level Directory entries for the same host. Multiple top level Directory entries may result in lower restore time, if a user is seeking to restore individual files within those Directories.
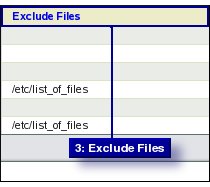
- Box 3. Exclude.
- Files to be excluded from the Backup are specified in Box. 3.
- If users want to exclude more than one file, enter a regular expression or enter the path to a file that contains the full list of files to be excluded.
- Box 4.Encryption and Compression
- These two choices can be made in Box 4.
New Edit Duplicate Delete
- New Edit Duplicate Delete Buttons:
- New and Edit Buttons
- New or Edit buttons clicks take users to a different page where a user can enter or edit the information.
- This is discussed in detail a little later under 'New or Edit Buttons' section.
- Duplicate Button
- On clicking the Duplicate Button, for each check box that has been ticked, a Duplicate entry is added to the list with expression _copy added to the host name.
- This does not create a Duplicate Backup Set.
- It merely creates a duplicate DLE that needs editing.
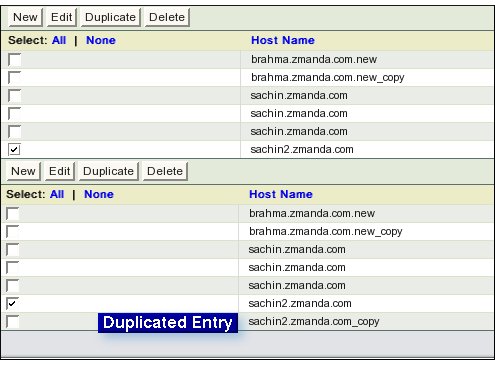
- De-select the original entry and select the Duplicate entry for editing. Please see Edit Button section on how to rename the Duplicate Disk List Entry.
TIP: Duplicate is useful if a user has named the Hosts in patterns like ABC1, ABC2, ABC3 etc. It is also useful to specify different exclude files and Encryption/ Compression options on the same host.
- Delete Button
- Select the entry to be deleted by ticking it.
- Click the Delete Button.
- The ticked entry is silently deleted on the click of Delete Button.
- There are no warnings and no way to undo the delete.
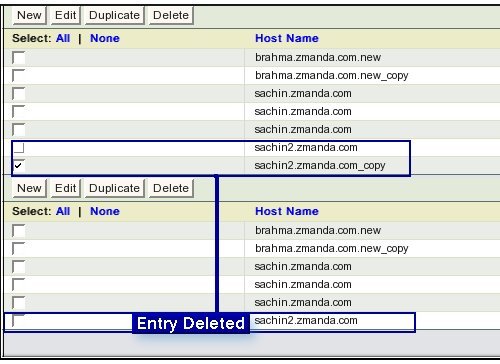
- A user needs to create a fresh entry to undo the wrong delete.
Host and Directory Names
- Host Names are made up from Alphanumeric characters.
- They can also include either one of the two special characters, the period '.' or the dash '-'.
- These special characters need to be included in between the usual Alphanumeric characters.
- When Duplicate Button is clicked, the duplicate Host Name has the string '_copy' attached to it.
- This name is illegal and a user is expected to edit it to a legal name.
- There can be multiple Disk List Entries with the same Host Name.
- However the combination of Host Name and Directory must be unique.
- Directories Names have to follow the naming conventions of the host.
- All sub-directories and their content will be backed up when a directory is specified.
- Host Names are made up from Alphanumeric characters.
Tip: Having Multiple Host cum Directory combinations with different exclude list and Encryption and Compression options optimizes Backup and Recovery.
Exclude Files
- 4. Exclude Files
- Exclude file is an important component in optimizing the performance of the Backup set.
- ZMC uses GNU-tar utility which supports exclude lists.
- If a user specifies a Host name and the root directory, ZMC will backup everything on that server.
- It will uniformly Encrypt or Compress the data on that host.
- ZMC allows a user to specify only one wild card expression or the path to an exclude file per Disk List Entry.
Some simple examples: Exclude any file or directory that ends in ".log" e.g. ppp.log, XFree86.0.log *.log Exclude any file or directory with the string "log" e.g. logfile, maillog, syslog, ppp.log,XFree86.0.log *log* Exclude any file or directory that starts with string "cron" and ends in ".gz" e.g. cron.1.gz, cron.2.gz, log/cron.1.gz *cron*.gz The question mark can be used to specify a single character. e.g. log.1, log.2, log.?
- The exclude list file should reside on the client-host to which it refers. Hence the path to the exclude list must be in reference to it.
- The exclude list file can be named anything that pleases a user and can be created with any text editor.
- It should have only one exclusion entry per line.
- Advantages of exclude files option.
- There are two different uses of exclude file option.
- Firstly, a user wants the excluded data not be part of any Backup Set.
- Such data tends to be quite small in quantity and does not save much.
- Secondly, the exclude list operates to exclude the data from Compression or Encryption options.
- A user saves on precious CPU cycles, network traffic, and size of backup window.
- There are two different uses of exclude file option.
- If the data on the host is organized in such a manner that implementing multiple top level directories in different disk lists makes no sense, exclude lists may allow a user to organize the backup with possibility of faster restore for some files.
Encryption and Compression
- 5. Encryption and Compression Choice
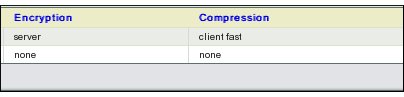
- Under the page entered with New or Edit Button, users will be able to set/edit if they want Encryption and Compression to the Host/Directory combination.
- User's choice will be displayed on the BackupWhat page.
- Compress files.
- ZMC compresses the data on the Client.
- This results in lesser bandwidth being consumed while the Backup image is being transferred to the Backup server.
- ZMC supports compression using gzip and the data can be uncompressed almost universally.
- Many Tape drives have built-in hardware compression.
- There are many advantages in allowing that hardware to handle the compression task.
TIP: Anticipate difficulties of uncompressing backed up data when a device that uses proprietary compression algorithm fails. A user may also face difficulties when that device is no longer in use/usable. For images and other pre-compressed files,do not waste Backup time trying to uselessly compress them.
- Encrypt files
- Usually backed up data is not guarded with as much care as live data is.
- Encrypting such data adds a layer of protection against misuse.
- ZMC encrypts the data on the server.
- It uses amcryptsimple encryption.
- Encryption passphrases are stored in amandabackup user directory on the server.
New or Edit Buttons
- New Button
- Users do not have to select anything before clicking the New Button.
- Users are to enter all the details of a Disk List Entry on the page that opens on clicking the New Button.
- New Button
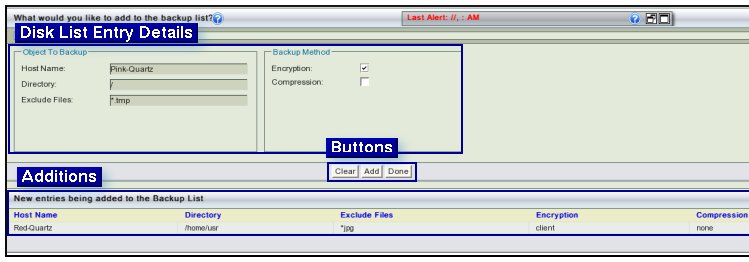
- The details users are expected to enter are:
- 1.Host Name
- 2.Directory Name
- 3.Exclude Files
- 4.Encryption Yes/No
- 5.Compression Yes/No
- Host Name:Enter the name of an existing host on the Network.
- Please note that other than Alphanumerical characters [Aa-Zz][0-9], A user can use only the period “.” and the dash “-” as middle part of the name.
- Users will be warned of an invalid name when the Add Button is clicked.
- Till users click the Add Button, they can go back to any box and alter its entry.
- Clicking the Clear Button will delete all unsaved details in one go.
- Users can enter more than one Disk List Entry details on the page.
- Just click the Add Button after each entry.
- It will be added to the list at the bottom of the page.
- Click Done Button to save and go back to the Backup What page.
- The details users are expected to enter are:
- Edit Button
- Users have to select the Disk List Entry that they want to edit before clicking the Edit Button.
- On the Edit page that opens, the existing entry is displayed at the bottom.
- Edit Button
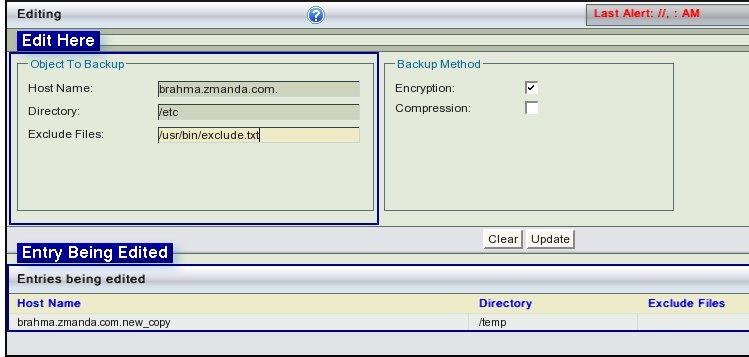
- The same contents, ready for editing are also displayed above.
- The Illustration shows that the host name has been edited, with '_copy' string at the end of its name, deleted.
- It also shows that the Directory has been changed from /temp to /etc.
- Exclude file name is being entered.
- Click Update Button to end the editing.
- Users will be taken back to the previous page, where the edited entry will be shown in its original place.
Move to ... Option
- To continue the process of setting up a Backup Set, please move on to Backup Where option.
- If users are editing only the Backup What part of an existing Backup Set, please move on to Verify option.
